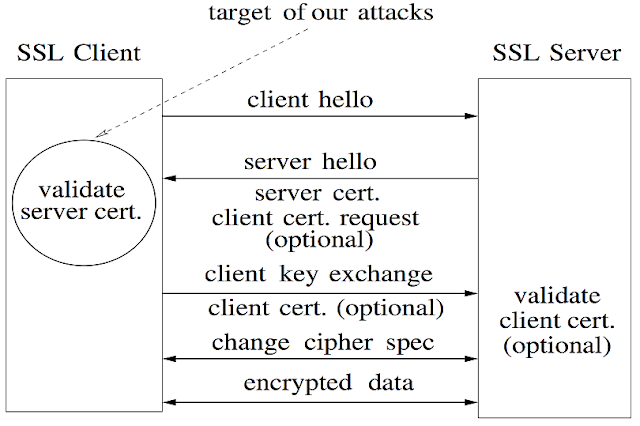
 |
| Fig. 1. How SSL protocol works between Client and Server |
However (as you know, the main article starts here), many existing non-browser software components do not really care such a SSL's certificate validation process. The researchers found that there are so many well-known IT companies who just had no idea how SSL works, and what they are skipping when using SSL protocol. If you're a user of web-payment solutions, and/or online e-commerce platforms, you'll be say "No Way!!!" in 5 seconds when you read the next paragraph of this post.
Here were the companies who skipped the SSL certificates by accidents (or, mistakes): Amazon, Paypal, AIM, FilesAnywhere, Rackspace, TextSecure, Trillian, Lynx Browser, Tweepy, AdMob SDK, ZenCart, osCommerce, Ubercart, PrestaShop, and sort of Apache open-source projects.
- note that, most of them were fixed their code right before/after when Prof. Dan Boneh's published paper was presented at ACM CCS'12.
 |
| Fig. 2. Protocol stacks and their software libraries |
Here is an example; if you are using a libcurl (cURL library), you should be able to turn-on the optional parameters for SSL certificate validation. Here are two optional parameters and their setting values to validate SSL certificate:
- CURLOPT_SSL_VERIFYPEER = true
- CURLOPT_SSL_VERIFYHOST = 2
(NOTE THAT, THIS IS AN INTEGER, NOT BOOLEAN.)
Actually, libcurl has very bad documentations, but recent libcurl (7.10) made a 'Good' default settings, so that all the two parameters are set by default. Thus, we shouldn't have any problems on validating SSL certificates.
However, there are still many software components using older libcurl (<7.10), and the developers usually make mistakes like PayPal did:
| Fig. 3. PayPal's initial code on libcurl optional parameter setting for SSL certificate validation |
| Fig. 4. PayPal's second mistake on optional parameter setting for SSL certificate validation |
Similarly, Python has really simple (but bad for security) implementation on the popular library called urllib. Usually developers have lack of time to do coding, so they usually do not thoroughly (or, carefully) read the documentations. But on the documentation of the urllib, there is a disclaimer (warning) for developers using this library: (READ THE WARNING ON THE PINK BOX)
 |
| Fig. 5. Warning message on the urllib library |
Since I had an experience of "theft of my credit card numbers in wired communication" when I was living in France in 2010. During the time, I bought some goods via several web-sites, and I now suspect that there were the same or similar problems.
I also hope that there were no identity thefts from the Amazon and PayPal payment systems.
If you're interested in reading more specific information, please refer to this original article in HERE.
- written by ANTICONFIDENTIAL, at SF, in April 19, 2013
0 comments:
Post a Comment